Careless user actions are why many cyberattacks are successful. Research shows that with regular security awareness training, midsize enterprises will experience fewer security breaches. Midsize enterprise CIOs can protect company systems and intellectual property by influencing secure behaviour. Security and privacy awareness and training is an important aspect in protecting the Confidentiality, Integrity, and Availability (CIA) of sensitive information.
Key Findings from several studies suggest:
- More than half of breaches are a result of employee behaviours that were unsecure or inadvertent.
- Confidential data, intellectual property and digital systems are only as secure as their weakest users.
- Organizations run the possibility of risk management strategies being less effective without an awareness program.
Establishing and maintaining information-security awareness through a security awareness program is vital to an organization’s progress and success. A robust and properly implemented security awareness program assists the organization with the education, monitoring, and ongoing maintenance of security awareness within the organization. This guidance focuses primarily on the following best practices:
- Organizational Security Awareness: A successful security awareness program within an organization includes assembling a security awareness team, role-based security awareness, metrics, appropriate training content, and communication of security awareness within the organization.
- Security Awareness Content: A critical aspect of training is the determination of the type of content. Determining the different roles within an organization is the first step to developing the appropriate type of content and will also help determine the information that should be included in the training.
- Security Awareness Training Checklist: Establishing a checklist helps an organization when developing, monitoring, and/or maintaining a security awareness training program.
Best Practices in Organizational Security Awareness
Security awareness should be conducted as an on-going program to ensure that training and knowledge is not just delivered as an annual activity, rather it is used to maintain a high level of security awareness on a daily basis.
Assemble the Security Awareness Team – The first step in the development of a formal security awareness program is assembling a security awareness team. This team is responsible for the development, delivery, and maintenance of the security awareness program.
Determine Roles for Security Awareness – Role-based security awareness provides organizations a reference for training personnel at the appropriate levels based on their job functions. The training can be expanded upon—and subject areas combined or removed—according to the levels of responsibility and roles defined in the organization.
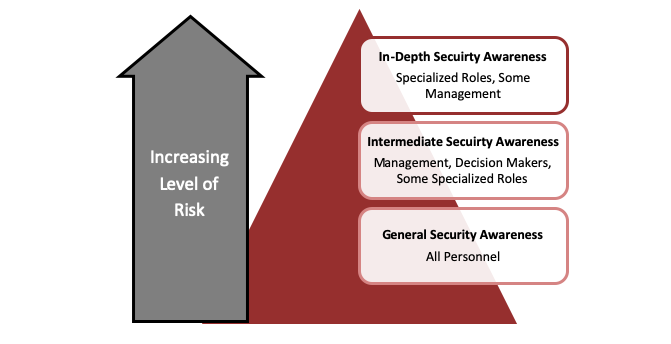
Security Awareness throughout the Organization – The key to an effective security awareness program is in targeting the delivery of relevant material to the appropriate audience in a timely and efficient manner. Management leadership and support for the security awareness program is crucial to its successful adoption by staff. Managers are encouraged to:
- Actively encourage personnel to participate and uphold the security awareness principles.
- Model the appropriate security awareness approach to reinforce the learning obtained from the program.
- Include security awareness metrics into management and staff performance reviews.
Security Awareness Training Content
Training materials should be available for all areas of the organization. Security awareness and training materials may be developed in-house, adapted from a professional organization’s work, or purchased from a vendor. There are security awareness vendors that provide prepared materials such as computer-based training (CBT), posters, and newsletters.
Below is an example of content that is commonly included in general security awareness training:
- Organization’s Security awareness policy
- Impact of unauthorized access (for example: to systems or facilities)
- Awareness of security requirements for different payment environments
- Importance of strong passwords and password controls
- Secure e-mail practices
- Secure practices for working remotely
- Avoiding malicious software – viruses, spyware, adware, etc.
- Secure browsing practices
- Mobile device security including BYOD
- Secure use of social media
- How to report a potential security incident and who to report it to
- Physical security
- Dumpster Diving
Security Awareness Program Checklist
The information listed below may be used to assist with security awareness training and education planning.
- Creating the Security Awareness Program
- Identify compliance or audit standards that your organization must adhere to.
- Identify security awareness requirements for those standards.
- Identify organizational goals, risks, and security policy.
- Identify stakeholders and get their support.
- Create a baseline of the organization’s security awareness.
- Create project charter to establish scope for the security awareness training program.
- Create steering committee to assist in planning, executing and maintaining the awareness program.
- Identify who you will be targeting—different roles may require different/additional training (employees, IT personnel, developers, senior leadership).
- Identify what you will communicate to the different groups (goal is shortest training possible that has the greatest impact).
- Identify how you will communicate the content—three categories of training: new, annual, and ongoing.
- Implementing Security Awareness
- Develop and/or purchase training materials and content to meet requirements identified during program creation.
- Document how and when you intend to measure the success of the program.
- Identify who to communicate results to, when, and how.
- Deploy security awareness training utilizing different communication methods identified during program creation.
- Implement tracking mechanisms to record who completes the training and when.
- Sustaining Security Awareness
- Identify when to review your security awareness program each year.
- Identify new or changing threats or compliance standards and updates needed; include in annual update.
- Conduct periodic assessments of organization security awareness and compare to baseline.
- Survey staff for feedback (usefulness, effectiveness, ease of understanding, ease of implementation, recommended changes, accessibility).
- Maintain management commitment to supporting, endorsing and promoting the program.
- Documenting the Security Awareness Program
- Document security awareness program including all previously listed steps within “Creating the Security Awareness Program,” “Implementing Security Awareness,” and “Sustaining Security Awareness.”
Kanoo Elite help customers close data security and compliance gaps to avoid data breaches. We provide information security services and are certified to help customers achieve security and compliance standards.
We are an information security services provider with years of information security experience. We help businesses achieve information security maturity through our advisory and technology capabilities.