The drive to improve operations efficiency, performance and quality of services is behind the interest to leverage elements of IT infrastructures (such as Internet Protocol [IP]-based communications) within OT environments. As physical and cyber befriend one another, so too must efficiency and security. The two need not be at odds, and in fact, companies should factor both into the production cost-benefit equation sooner rather than later. But before they can secure anything, they need to know what that “anything” is.
One major constraint to protecting industrial systems—even for industrial companies themselves—is a misunderstanding of the difference between information technology (IT) and operational technology (OT). It remains a hazy area in terms of if and how the two overlap, where they diverge, and who, with regard to internal security teams, is responsible for securing what.
Here’s an easy—if overly simplistic—way to think about it. IT stores, retrieves, transmits, and manipulates data. OT uses that data to monitor, control, and operate physical devices, processes, and events. In the past, OT systems were not connected to the Internet. Today, everything’s changing, and because of that, not only must new OT vulnerabilities be addressed, but companies must decide who’s to address them and how.
Increasing replacement of OT infrastructure with IT systems is opening new vulnerabilities and risks that are pushing security and risk management leaders to update security approaches and strategies. This research note will help security and risk management (SRM) leaders, tasked with the coordination of securing these converging IT/OT environments, to develop a suitable architecture to align to the new emerging security requirements for securing networks and endpoints in converged IT and OT environments.
Analysis
Focus on Safety and Reliability as Security Strategy Adapts to Converging IT and OT
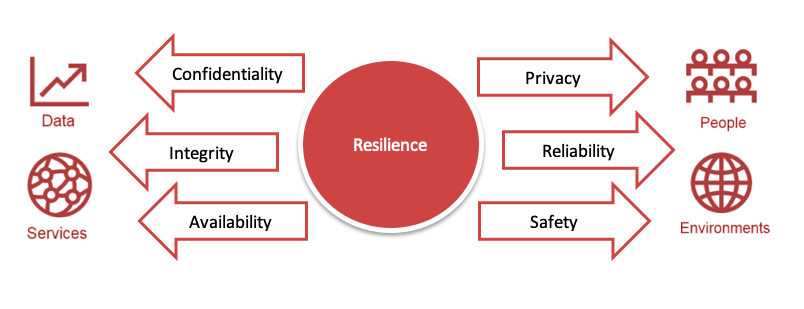
To achieve safety and reliability, security must seek and establish collaboration and an organizational structure that involves both IT security and OT competencies. This will help align security to safety practices and regulatory requirements. SRM (security and Risk Management) leaders need to revisit security processes and policies in order to extend a security strategy beyond the traditional pillars of confidentiality, integrity and availability (the CIA model), focusing on data security, but also including reliability and safety.
Factors Driving Interest to a Centralized and Coordinated IT/OT Security Strategy
- Wide Range of Industry Verticals Impacted by OT-IT Convergence – With the emergence of new digital initiatives, such as smart cities, industries that traditionally haven’t been focusing on OT a great deal have increased their interest toward tackling such new risks.
- Value of Air Gap as a Main Approach to Securing Merging Environments – In the most extreme circumstances an air gap can be used to completely isolate two domains. This approach has been a traditional pillar for securing OT environments.
Consider a Hybrid Architecture of Traditional Security Technologies and Specialist Controls to Protect OT Environments
Finding the right balance between utilization of traditional security controls, such as firewalls, and OT specialist security tools is key. SRM leaders would need to assess the specific security requirements different OT environments would present and then decide which approach and tools to select, depending on the security requirements.
Securing OT Networks
The following traditional security controls offer critical capabilities within OT environments:
- VPNs/firewalls— A key value for firewalls is to enable a bidirectional communication between the IT and OT environments. Such equipment is typically used to have better control of access between IT systems and OT environments.
- Intrusion detection system (IDS)/intrusion prevention system (IPS)— The increasing exposure of OT environments to cyberattacks is resulting in an increasing need to apply a detection strategy alongside the network segmentation function provided with firewalls. Both IDS and IPS equipment should be considered to provide situational awareness toward detecting potential attacks.
- Network access control (NAC) — The same NAC technology that is used in many IT environments can also be implemented to improve the availability and reliability of OT networks. SRM leaders should particularly look at two areas where NAC that can provide most relevant value within OT environments – Device profiling and policy Enforcement.
- Deception — With the availability of a range of products allowing for the passive monitoring of attacks through the implementation of deception technologies, there is now the opportunity to utilize such tools within OT networks. Below we list some of the most popular and effective OT specialist controls to secure OT environments that SRM OT security leaders must consider:
- OT asset discovery/monitoring
- OT vulnerability management
- Unidirectional gateways
- Securing OT Endpoints — Endpoint security is the other critical area that SRM leaders, strategizing on OT, should focus on. This is particularly the case as OT-based endpoints are increasingly unable to take advantage of air gapping from IP-based systems due to converging IT/OT.
- Patch management — Develop an OT-specific patch management process that includes a check with the equipment vendors to address issues before patch deployment.
- Device control — SRM leaders should consider adding an extra layer of security for all OT endpoints, even those benefiting from physical separation through air gapping.
- OT endpoints inventory — SRM leaders, looking at improving OT security, need to implement a strategy aimed at improving OT endpoints and systems visibility in order to better understand what needs to be protected and prioritized.
- Application control — Alternative risk-mitigating measures should also be considered for OT endpoints through limiting activities of OT-based endpoints to essential tasks.
Evaluate Existing Framework Models as Part of a Step-by-Step Approach to Coordinate an IT/OT/IoT Security Strategy
Reviewing and adjusting a security architecture is challenging. As a result, SRM leaders should consider and review available examples of security architectural models. There are several good security frameworks that can be considered as a reference model, with the following approach:
First, start off with a risk-based assessment of OT environments based also on an accurate asset inventory and vulnerability assessment. The NIST Cybersecurity Framework (CSF) and the Australian government security framework offer good guidance toward a risk-based approach addressing both the digital and physical aspects of an organization in their approach to security.
Second, review the different security frameworks available, and upon selecting the most appropriate, create a plan of action to develop a security policy and architecture that takes into consideration the security requirements arising from converging IT and OT.
Apply All Stages of an Adaptive Security Architecture to OT
The concept of adaptive security is based on the idea that preventive measures alone are not enough at a time of increasingly sophisticated targeted attacks, where the likelihood of being breached is very high for any organization. This concept also has relevance when planning to secure OT environments, particularly at a time of OT convergence with IT. The four stages of the Adaptive Security Architecture is designed as follows:
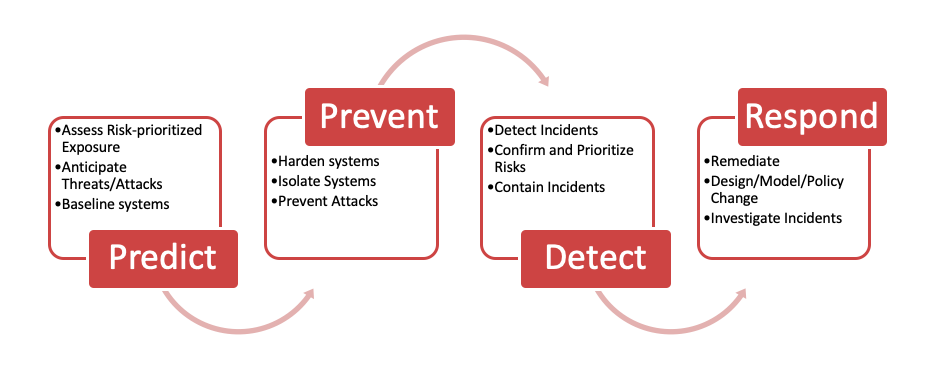
A typical assessment entail:
- Information gathering and documentation relating to an organization’s people, architecture, and technology.
- Review and analysis of documents detailing network configuration, topology, policies, and other relevant aspects unique to an organization
- Onsite interviews and inspection with subject matter experts for additional technical and contextual understanding not apparent from documentation reviews alone
- Onsite technical testing to assess and evaluate the cyber security posture of assets
- Offline data analysis and application of best practices methodology to assess risks
- Risk assessment to identify sources of vulnerabilities, determine security posture, prioritize potential risks, and provide remediation roadmap
- Findings report to include recommended mitigations based on prioritized risks
Securing an operational technology (OT) environment is significantly different than securing a traditional information technology (IT) environment. What you’re securing is different, and how you secure it is different. IT focuses on digital information protection. OT focuses on people and physical asset protection.
Kanoo Elite provides a proactive and transformative approach to OT security. We deliver security solutions specific for OT with an industrial mindset, purpose-built technology, and specific OT security expertise. Our solution covers the entire converged IT-OT network to close OT security gaps, deliver full visibility, and provide simplified management integrating your most valued resources—people, environment, and assets. Kanoo elite is the only vendor that can deliver a true integrated Security Fabric that covers the OT security best practices and requirements for the entire converged OT-IT network.



