Introduction
Building an effective and comprehensive security awareness program seems like a daunting task to those who are fortunate enough to be responsible for it. There is a lot of information at your fingertips, but how do you turn that information into something useful? Like most security awareness professionals, understanding a program’s critical components and connecting them together to design something comprehensive, continuous and engaging is an overwhelming task. It is a task we are taking on head-first in this white paper in order to provide you with a strong blueprint to get started.
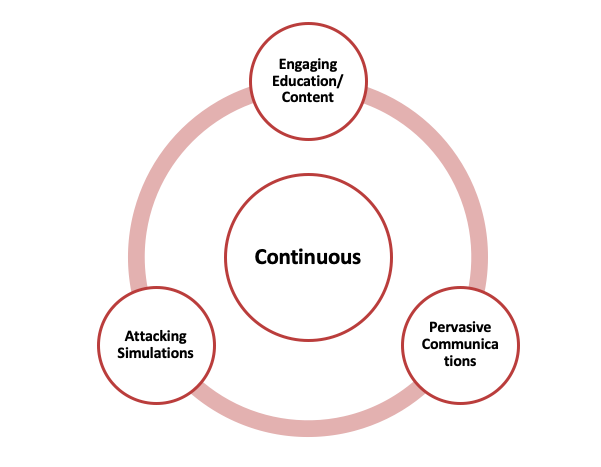
We generally assume that a one-size-fits-all approach to driving security awareness throughout our enterprise will improve security performance. However, much more than a single, generic education program is required to drive effective awareness. In order to provide an effective security awareness education program, leaders should recognize that there are three key elements that form the foundation to a successful program:
- Knowing your audiences and utilize Education Tools to help the audience understand their responsibilities in protecting the enterprise, coupled with reinforcement tools designed to change long-term behaviours.
- Continuous and topical communication – Communication/Interactive tools for ongoing reinforcement, rewards for good behaviours and to keep security top-of-mind.
- Interactive education on security tactics – A way to identify key pockets of risk (such as awareness/training fatigue) within the enterprise audience and deliver simulated exercises to test their ability to detect social engineering attacks.
Analysis
For implementation of an effective Security Awareness Program, do consider the following factors:
- What Is Your Starting Point? – To start, determine where your program originates.
- What Are You Trying to Do? – Determine your Objective.
- Who Are Your Advocates? – Analyse your Audience.
- Engaging Content and Communication – Utilize large libraries of computer-based security awareness training content; including interactive modules, videos, games, posters and newsletters.
- Simulated Phishing – use simulated attacks to test your audience’s ability to detect, report and prevent a cyber-attack.
- Build an Army – Develop a Security Team.
- How Is It Going? – Quantify the success of your security awareness program.
For a better understanding of the above pointers, the following descriptions are provided to provide you a comprehensive approach towards an effective security program.
Assessing the Culture of the Enterprise for an effective Security Awareness Information
Training sessions that include security policies are easily quantifiable. Nevertheless, comprehensive security communications programs that leverage a variety of media and content styles produce demonstrable improvements in levels of employee security awareness. By combining education with assessment of vulnerable areas and constant communication of important practices and new considerations, we can engage effective security awareness.
Leveraging an Attack Simulation System as a Requirement Analysis Program
A strong, unique approach to education is important when traditional security content is boring, complicated and sometimes scary. Determining the best approach depends a lot on the culture of the enterprise. Partnering with a vendor that can provide many different versions and flavours of content will not only assist in making sure that the content is the right fit, but also that we have options for future training/retraining.
Increasing the frequency of trainings for employees while decreasing the time they spend in training will affect the Enterprise effectively. Behavioural management systems can serve this purpose, by including attack simulation products that mimic phishing, USB drops and SMS-based attacks. Behaviour interruption covers DLP, WebProxy, endpoint detection and response scenarios. Reinforcement includes automated behaviour-centric enrolment in relevant training. We should also test several kinds of training and content to ensure that they are using the most effective materials for their audience.
The use of a phishing simulation program is important to help identify key pockets of risk within the enterprise audience, deliver social engineering attacks and provide just-in-time training and teachable moments. Establishing corporate email policies ensures that employees and customers are aware of what a legitimate email looks like and increases security awareness.
Baseline Testing
We need to do a baseline test of the organization two to three times prior to launching an official security program, in order to get a true understanding of where risk lies. The workforce does not need to be informed of the results as a teachable moment. Then the management can administer the program based on the identified risk. The high-risk groups — executives and their administrative assistants, IT, finance and recruiting — should be phished more frequently that the others. We must tailor your program so that it is targeted and delivers the right amount of training, with the right frequency.
Use Communications and Marketing Tools for Ongoing Reinforcement of the Program
Effective internal communications are about using memorable, compelling content and delivery to catch and maintain the interest of the audience. We can consider building a communications campaign with a mix of digital banners, web events and techniques messaging to help reinforce lessons. These include intranet messaging, holding online meetings and town halls and broadcasting security expert meetings. Award programs can praise good behaviour. The more people are exposed to the message, the better consumption will be.
Conclusion
Kanoo Elite is a GCC-based, world-class technology, consulting, and outsourcing firm leveraging deep technology expertise, strong industry experience, and a comprehensive portfolio of security services. Our team of highly skilled professionals have over 4000 years of combined experience to provide you with an effective security awareness training program which would be both comprehensive and continuous. Our design led approach to provide holistic services will leverage engaging/interesting content, simulated attacks and insightful communications and assist you to build a force of champions, advocates and executive support, for an effective Security Awareness Program.