Threat Intelligence products and services provide information and information about security threats and other security related issues. The smart-guided steps provide information about the identities, motives, features, and methods of the threatening players and, most importantly, give you the options to apply this to your online security systems. This information is based on technical sources (for example, network traffic and files downloaded from malware) and human resources, including cybercrime and scam scams, networking and law enforcement activities, incidental involvement, and collaboration with industry groups to share. in the industry.
Market Description
The scary intelligence market is made up of vendors who provide technology and services that allow the management and control of threatening intelligence. TI technology is referred to as threat platforms, which can be marketed as standalone solutions or as part of SOAR solutions. TI services may include explicit (above) web monitoring, dark web and deep web, delivered via feed such as MRTI and / or HUMINT reports. This may be provided directly to TI vendors or traditional content (sometimes premium) through various vendor technology vendors SIEM, EDR, IDPS, NGFW, SWG, SEG and CASB, to name a few.
The diagram below shows the normal life cycle of intelligence, and it is important to note that while this is just the beginning, this process is repetitive and should be self-evaluating. As needs change / change, so should your data acquisition, integration, and implementation plans.
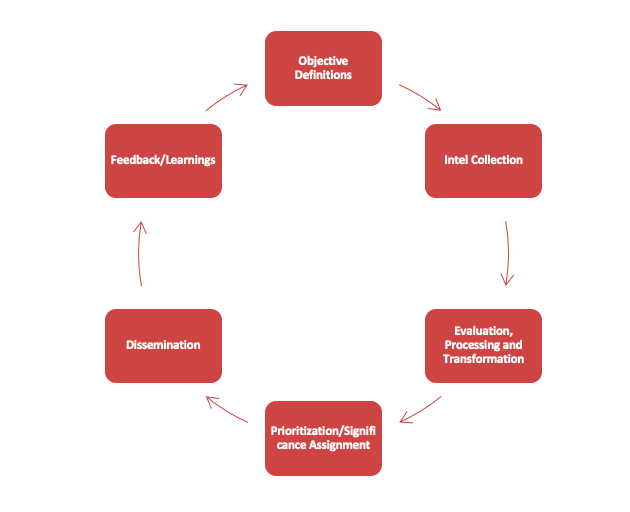
The threatening intelligence market remains large, with a growing number of vendors bringing a range of skills. Although incomplete, this number can be defined as being able to help three or more people (people), to help improve / accelerate the process by up to three or more processes, and to help develop three or more existing technologies.
Market Analysis
TI service customers often have valuable assets (for example, financial assets, assets, or assets that support critical infrastructure), protected or sensitive information (such as user ID or shared security information), usable services (e.g., network bandwidth), or customer bases large. Information obtained from a product or service usually goes into the planning cycle for many years and is sent to their security systems. TI services are very attractive to large businesses with significant product presence or high-risk profiles, and often have security organizations with mature security systems in place.
Vendors Often Consume Similar Information
Clients who decide to purchase services from multiple providers to integrate information from different sources should ensure that the resources are truly different. Vendors share some intelligent content or use OEM-type trading relationships. This does not mean that the offering of one seller is the same as that of another; it simply means that some of the content will be normal because it comes from the same source. Vendors do this to provide a larger content or rich content for a particular offer, especially if a shared partner is working in a different market or offering a different service covering a different part of a threatening environment.
Vendor Capabilities Vary
The collection, processing and analysis of crude information is a service provider. Depending on the needs of your organization, the ability of the vendor in the following areas will be important decisions:
- Whether the content is based solely on telemetry from the current network / host activity, or whether the merchant is accessing the dark web and appears to be threatening the actor’s work.
- Whether the content is collected only from open sources or includes closed (non-public) sources.
- Whether crude information is harvested from English-only sources, or the seller collects and interprets non-English sources. There is an undeniable political and ethical environment in the advanced services of TI, and its key security leaders are looking to take this requirement if it is needed in their intelligence system.
- Whether the vendor provides a series of individual data points or, alternatively, link and analyse different data points and reach informed conclusions.
- Whether the vendor has the ability and ability to make the content more relevant to threats and threats (for example, infrastructure attacks or intimidating characters) your organization must control.
- Whether the marketer distributes content in a way that your organization can use.
Popular TI Use Cases
Use-case-centric monitoring is still a good and effective way to start a journey and improve your defence system with smart-led measures. In other customer inquiries, we have seen customers first receive the service first, and then try to earn that amount to meet future use conditions. Instead, we recommend that you decide what you want in the TI in the first place – that is, what conclusion do you have in mind? Then decide what you will be able to do or spend extra money on your security budget.
Below, a list of the most used Intelligence cases:
Capture and Leverage What You Create
The long-term bottom line is for organizations to use the TI they see and create for themselves. This is usually a good place to start investing your time. Organizations often shoot novel intelligence that threatens themselves. Things like malware sandboxes and other technologies like deceptive technology all produce important threats.
Phishing Detection
Theft of sensitive information is a dangerous and common threat that is always an effective means of accessing organizational resources. TI can assist in identifying aspects of identity theft campaigns to speed up detection / response actions and assist with effective measures, such as prevention / prediction.
Threat Hunting
While exploiting threatening threats to point out a bad job, threatening hunting is a major source of intelligence as a stand-alone option. Tricks, tactics, and techniques (TTPs) are often harvested through engaging in hunting, whether by internal resources or outsourced to a retailer focusing on threats. It is important for internal threats to plan how TTPs and strategic indicators will be harvested, processed, and stored in the intelligence life cycle. Deciding to exclude threatening hunting activities also requires careful planning of the collection to ensure that the hunting service brings the findings to working. It is also worth noting that most affiliate marketers and respondents support cases of using hunting that threatens their clients.
Vulnerability Prioritization
Some common risk assessment tools now have this capability. However, it was led by small retailers of pure-play vulnerability prioritization technology (VPT). These vendors take risk assessment telemetry and use OEM TI (Risk-Based Security and Recorded Future are popular options), to allow the use of advanced novel analysis to provide a world-class threat view of this information presented in your organization context.
Surface, “Deep” and “Dark” Web Monitoring
The deep web is often part of a network that ordinary users may not be able to access (such as the onion router [ToR] or the Invisible Internet Project [I2P] sites and provides a great knowledge base for upcoming threats.
TI Analyst Augmentation
Some services provide dedicated or temporary access to TI analysts for your security system. This is a relatively new role for many security organizations. Only 1% of organizations with roles or responsibilities listed on other employees in their groups. They may be offered specific TI-related tasks that are specific to your organization.
TI Sharing
It is now well understood, but it is not particularly evident in public that TI sharing networks have a real number of security features. Traffic Light Protocol (TLP) is a level-based approach that facilitates the sharing of information. TLP describes methods for marking and classifying information, to suit different audiences.
Threat Actor Tracking
This approach is to get into a scary model to understand who, what, why and how. Officially, this describes the Diamond Model, organizations that use force to determine a character based on historical “battles” by responding to an incident or co-operation of a hunting hunt with a group of dangerous characters.
Intelligence Analyst Investigations Tools
One unusual thing that is often overlooked in TI is the use of specialized tools that analysts rely on daily results. These tools are widely used by intelligence analysts, security services, threat hunters, incident responders and intelligence experts.
Adversarial Misinformation Campaigns
The emerging consumer case is the ability of intimidating actors of various levels of expertise to launch inaccurate information campaigns for the benefit / harm of end user organizations. Analysis of a few inaccurate information campaigns revealed a pattern or method that threatening players use to make a profit or hurt organizations.
High-Level items to consider when considering Threat Intelligence
Consolidation Scope
What are the threats, what are the conditions of use that the provider can bring and what factors (MRTI, reports or access to the threatening analyst)? For example:
- What threats do they make?
- Are they focused on phishing scams, malware, deep / dark web, social media?
Depth and Accuracy
Most importantly how much information is available and how that information can be directed to you directly. At the same time, having a high level of honesty based on action is essential. Some TI flavours can age with time frames measured in hours.
Performance
How long has the provider been in the market? How does this work? If the customer base is doubled, can it help you with the same level of satisfaction? Is it financially viable?
Extension
Are you able to use TI in many ways, in different processes and within a set of tools? Another TI comes with a “black box,” which can be defined as a single object or a single use. If you want / need to use TI for many tools and processes, having it available in ways and formats that support this is a must.
Professionalism
Many TI providers are in-depth experts in specific areas and methods they use to understand the threat situation. Understanding this specialty is important. It will help you tailor the provider’s skills the way you need to deal with the risks you need help with.
Kanoo Elite, with its years of experience in providing threat management structures and assisting organizations to protect their environment, we are industry leaders to help you formalize your threat management plan to better anticipate and manage threats facing your organization. Our programs cover at least three key functions: threat intelligence, threat model, and security statistics. Collectively, with these capabilities, we help your Information Security operations prioritize controls that address real threats, detect incidents quickly, and make threatening intelligence more effective in your organization. Our threat management solutions also inform a wide range of security functions such as risk management, strategic planning, staff awareness, and board reporting.


