Data loss prevention (DLP) is a set of tools and processes used to ensure that sensitive data is not lost, misused, or accessed by unauthorized users. DLP software systems classifies regulated, confidential and business critical data and identifies violations of policies defined by organizations or within a predefined policy pack, typically driven by regulatory compliance such as HIPAA, SOC, PCI-DSS, or GDPR. Once those violations are identified, DLP enforces remediation with alerts, encryption, and other protective actions.
With so many security companies these days recognizing the importance of DLP in order to address the challenges of today’s cybersecurity landscape, it is difficult to choose vendors offering some form of a DLP solution, or products with DLP capabilities integrated in security products or SaaS applications, as well as cohesive enterprise DLP suites. With this article, we have illustrated the key differences between the two types of DLP – Integrated and Enterprise which will help you to choose the perfect deployment system.
Definitions
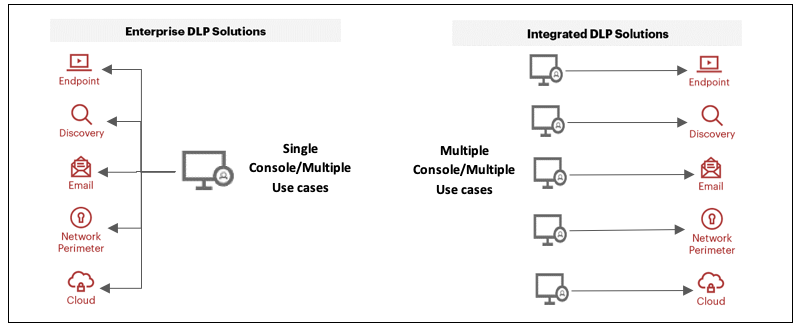
Enterprise DLP products generally incorporate more advanced content inspection techniques to identify complex content and apply remediation. Enterprise DLP products provide a broad and flexible deployment product set that is applicable to many diverse use cases, including regulatory compliance, internal policy compliance and intellectual property (IP) protection.
Integrated DLP products are natively integrated in appliances or services, such as a secure email or web gateway, a cloud access security broker (CASB), or an endpoint protection (EPP) product. They typically have limited policy and reporting capabilities and focus on the management of the DLP functionality in its single environment. Integrated DLP increasingly includes cloud provider native DLP.
Integrating DLP policy orchestration with other integrated or enterprise DLP products is a manual process. Integrated DLP deployments typically focus on regulatory compliance use cases.
Analysis
The following pointers will assist you to best guide your DLP strategy and choose the DLP system, most appropriate for your business:
Utilize Data Security Governance
Data security governance (DSG) is key to develop a successful data security strategy that includes DLP. It assists to assess and prioritize the business risks that may occur due to accidental data leakage or noncompliance issues. A proper evaluation of these data controls and policies requires communicating with the data owners and content creators involving multiple teams, including IT, security and business owners. Critical points to examine when contemplating integrated DLP or enterprise DLP include, but are not limited to:
- What resources are required to operate DLP on an ongoing basis, and will these resources be delivered by existing employees on staff, contractors or third parties helping staff or managed services for DLP?
- How many communications channels need DLP coverage? Email, web, content collaboration platform (CPP), FTP and secure file transfers?
- How diverse is the data? Is the data regulated or otherwise subject to compliance, or is the data intellectual property such as diagrams and formulary data? Is the data user-created unstructured data, semi-structured data such as form data or structured data?
- How complex is your data security policy? Do you have vastly different compliance needs across the organization or a diverse set of IPs?
- Are you heavily using cloud services as applications or data storage? Do you have a low number of on-premises file servers?
The answers to all these questions collectively will ultimately aid in choosing between integrated and enterprise DLP approaches.
Usage of Sensitive Data
Many organizations already have started utilizing existing DLP capabilities available in implemented security products. These integrated DLP capabilities provide with valuable insight into how sensitive data is moving into, across and out of the organization. The following controls are also considered:
Email Security Products
Email continues to be the most common use case for visibility into sensitive data usage, as part of data usage discovery and ongoing DLP strategy. Integrated DLP capabilities in email security products are common, and most provide a policy engine that can inspect the email message content and any attachments and apply security controls if the content matches configured rules. Examples of such controls include encryption of all messages that contain PII and financial data.
Secure Web Gateways
Along with email communication, web traffic and users posting information through applications like web mail and social media and posting content to non-sanctioned cloud services create an additional blind spot for organizations. Many of the secure web gateway (SWG) products, including cloud-based SWG services, offer built-in DLP and can look for activity such as logins to cloud storage, user access, sensitive data exchange with websites and web-based email services and provide deeper content inspection and analysis.
Cloud Access Security Broker
A Cloud access security broker, or CASB, is cloud-hosted software or on-premises software or hardware that act as an intermediary between users and cloud service providers. In addition to providing visibility, a CASB also allows organizations to extend the reach of their security policies from their existing on-premises infrastructure to the cloud and create new policies for cloud-specific context. CASBs have become a vital part of enterprise security, offering integrated DLP capabilities, such as pattern matching and document inspection. They also provide API and ICAP integrations with enterprise DLP products, so that the same on-premises DLP policies can also be exported and adopted.
Data Classification and Protection
Data classification and protection have grown in popularity due to the ability to “tag” content with a persistent metadata value, and have that tag persist throughout the life of the data. For example, these tags can also be used in conjunction with a lightweight agent on the endpoint to enforce policy based on the value of the metadata. Data security technologies, including CASBs, DLP and EDRM, can build on and adjust their DLP policies based on these metadata tags.
Endpoint-Focused Products
Integrated DLP is commonly available as part of EPP. The DLP component of EPP can look at user data actions including copy and paste, clipboard activity, removable media activity and printing of sensitive data. The integrated DLP agent in the EPP platform provides coverage for basic use cases and endpoint activity.
Summary
Enterprise DLP Deployment – if there is a Business Need for Strong Workflow and Unified Policies
Leverage enterprise DLP if your organization’s current or projected DLP requirements involve multiple use cases. Many buyers of enterprise DLP products are motivated by an immediate, compelling event, such as an embarrassing data loss or corporate, industry or government compliance need and are interested in the longer-term vision of granular control over all the data that flows around a modern organization. Enterprise DLP buyers with advanced requirements typically address endpoint, network data discovery, cloud and mobile use with a single unified platform and policies that work collectively for strong workflow and event correlation among data security events across the disparate DLP silos.
Integrated DLP Deployment – if you have Products with Strong DLP or Use Cases are Limited
Integrated DLP products appeal to organizations that are looking for cost-effective ways to solve one or two relatively simple data protection needs (such as email and network DLP), sometimes with products they already own. Integrated DLP is most effective in low complexity use cases with a single purpose. Policy management and event correlation fatigue will always be a concern when trying to get a unified view of DLP from multiple point products unless your specific use case is very basic.
Kanoo Elite with years of DLP Deployment experience, assists you to integrate a machine learning-based policy and rules engine with hundreds of pre-built rules,content discovery and classification for Personally Identifiable Information (PII), Personal Health Information (PHI), Personal Financial Information (PFI), and custom data types, built-in support for compliance and standards like GDPR, HIPAA, PCI DSS, ISO 27001, etc. Our DLP Deployment experts provides the best return on investment for organizations of any size; assisting SMBs, enterprises, and the public sector to address data loss, cybersecurity, and insider threats – all in an integrated suite.
Kanoo Elite also offers insights towards the possibility to mix and match functionalities, allowing organizations to eliminate tools which are superfluous to their needs. In this way, companies can cut costs while still maintaining some of the key capabilities of dedicated DLP such as highly customizable policies, centralized management and separate policies based on groups or departments.



